Incidental news: Cipher Mysteries recently had its 25,000th comment, while it has now also had close to three million page views. Which is nice. (Just thought I’d mention it in passing.) The remainder of the post is for tying up various Voynich threads that aren’t each enough for a whole post of their own.
Edith Zimmerman
Here’s a Voynich amuse-bouche: any page with drawings taken from the Voynich Manuscript’s Quire 13 that includes the following quote is more than OK by me:
Anyway, so then we got to the part in our performance where Shelly and Mathilde stand in giant pipes covered with rhinestones. They hold up large balloons that have fishtails dangling off them, Chinese dragon-style.
Voynich LOL
An example of the per-section language use in Voynichese is that the word EVA “lol” appears far more often in quires Q13 and Q20 than anywhere else. Here’s the lol cluster in the top paragraph of f77r (1 x loly, 3 x lol, all at the end of lines):
Aside from Q13, EVA lol also appears here: f48v f86v6 f103r/v f106r f107r/v f111v f113v f115r f116r. Incidentally, the first word of the last paragraph of f116r (which I suspect contains a colophon from the author) seems to me to be the same kind of thing as the heavily digraph-structured labelese words, though with the extra twist of EVA l sometimes standing in for ol, as I discussed elsewhere):
Brian Hendley
The recent talk of Canadian academics’ rogue AI’s preparing for the enslavement of Mankind by solving Voynichese triggered some memories in the head of Brian Hendley, a philosophy professor at the University of Waterloo:
Your recent story about deciphering the mysterious Voynich manuscript took me back to my graduate school days at Yale and my dissertation supervisor, Bob Brumbaugh. Bob was a recognized Plato scholar but he did have a crack at deciphering the Voynich manuscript, resulting in some published articles and a book, “The Most Mysterious Manuscript: The Voynich ‘Roger Bacon’ Cipher Manuscript.” I recall Bob saying that you could spend your entire scholarly career trying to decipher the Voynich.
Ain’t that the truth, eh? *sigh*
Gerard Cheshire (yes, again)
Polyglot linguistic Voynich theorist Gerard Cheshire (whose theory I discussed here back in 2017) has hurtled into 2018 even more convinced of his utter rightness (and of everyone else’s abject wrongheadedness).
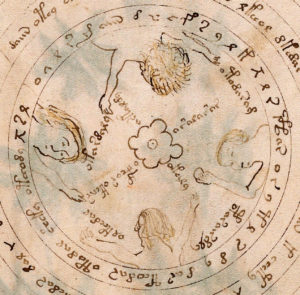
If you really, really want to read his all-new polyglot interpretation of the nine rosette page (which he calls “Tabula regio novem”, which I don’t believe is grammatical Latin, whatever Google Translate may say) which is all about Italian volcanoes, it is online here.
For those whose appetite for such things would be easily assuaged by a single dim sum, here is Cheshire’s elucidation (I hesitate to call it a decryption or translation) of the text around the bottom-left (SW) rosette:
om é naus (people and ship)
o’monas (in unity)
o’menas (take charge)
omas (mothers/babies)
o’naus (of ship)
orlaus [orlas] (to protect)
omr v asaæe [vasaie] (life-force pots: pregnant bellies)
or as (yet in)
a ele/elle a (he/she at)
a inaus [inauspitica] (inauspicious/unfavourable),
o ele e na (he/she is in)
æina (a/one)
omina (omen)
olinar (to look)
n os aus (it is)
omo na moos (man not mouse)
é ep [epousee] as (and embrace)
or e ele a opénas (an opening)
os as ar vas (thus you go)
opas (but carefully)
a réina (to the queen)
ol ar sa os aquar aisu na (to facilitate not getting wet with seawater).
J. Michael Herrmann
One little-noted Voynich theory from last year was J. Michael Herrmann’s The Voynich Manuscript is Written in Natural Language: The Pahlavi Hypothesis. Exactly as it says on the tin, it’s a linguistic Voynich theory:
Here, we provide evidence that the VM is written in natural language by establishing a relation of the Voynich alphabet and the Iranian Pahlavi script. Many of the Voynich characters are upside-down versions of their Pahlavi counterparts, which may be an effect of different writing directions. Other Voynich letters can be explained as ligatures or departures from Pahlavi with the intent to cope with known problems due to the stupendous ambiguity of Pahlavi text.
Herrmann followed that with his 2018 paper The Cannabis Page of the Voynich Manuscript. This finesses some of the claims in the 2017 paper, now suggesting that Voynichese uses an “alphabet that has similarities to Pahlavi and Mandaic script”.
The “Cannabis Page” referred to in the title is f16r:
In Herrmann’s translation (which is accompanied by extensive notes, presumably to help readers overcome the “stupendous ambiguity” of Pahlavi), the first paragraph of f16r emerges as a tirade against the evils of cannabis:
Cannabis [is] vain. Stay away from the impudent crowing man. The pipe is a debasement. Jaundice [is] the overly happy face of the adherent. [He is] puffed up with pride. Security does not come [to him]. In the evening peace of mind does not come [to him, as] the serpent of nightly lust spoils him. [What is] concealed,
will become public.
If you are interested, Herrmann’s rendering of the first paragraph of f1r is as follows:
(1) The humble grass shames you. Obediently hold the law. You cry for help for the tribunal commanded (2) for being insolent. Verily, you are frightened out of your wits by the troops in fury. Crowds and crowds of abled ones. (3) Woe, the well ordered line (of troops) is driving forward. If you see this, you will. Don’t start to count and to number the men, woe! (4) Refrain form [sic] the uneducated baldhead, the storyteller, the teaching of the “light bringer”. Remember the time of the fathers. (5) Heaven shield those who are weak for debasement. The man of doubt guide right.
If only I had an open letter I could use, if only… :-/