Essentially, a ciphertext is a piece of text where the individual letters have been transformed according to a rule system – substitution cipher rules replace the shape of the letters (as if you had just changed the font), while transposition cipher rules manipulate the order of the letters.
THIS IS A CIPHER —> UIKT KT B DKQIFS (substitute each letter with the one after it in the alphabet)
THIS IS A CIPHER —> SIHT SI A REHPIC (transpose the letters, writing each word back-to-front)
So, as long as (a) you know [or can crack!] the rules by which the “plaintext” (the original unenciphered text) was transformed, and (b) those rules can be played out in reverse, then you can decipher the ciphertext.
OK so far… but if you’re looking at historical ciphers, there’s a problem.
Prior to 1400, transposition ciphers were extremely rare, partly because words themselves were rare. Many documents were written without spaces – and without spaces, where do words begin and end? Effectively, this meant that in-word transposition ciphers (such as reversing syllables, as the Florentines Antonio Averlino and Leonardo da Vinci both used) would only happen in those few places (such as Florence) where people had a modern concept of what words were. A well-known modern example is “Pig Latin“, a (20th century) humorous in-word transposition cipher: and there’s the 19th century “loucherbem” in French, too.
Round about 1465, these flowered into some kind of complex system (by an unknown practitioner, and now apparently lost forever): Alberti, writing in Rome during 1465-1467, mentioned a number of ideas for a complex transposition system, though he recommended his own cipher wheel in preference to them.
Yet after 1500, these basically disappeared into the historical footnotes of cryptographic works. What replaced them (circa 1550) was the “rail-fence” Renaissance notion of transposition cipher: this was instead grounded in the print-centric culture of movable type. This saw messages as sequences of characters tick-tocking away to a metronomic beat (i.e. one per tick), and transposition ciphers not as a way of disrupting word contents, but instead as a way of disrupting (& subverting) the metronomic pulse of letters – a very different beast indeed.
THIS IS A CIPHER --> ISTHAY ISYAY AYAY IPHERCAY (Pig Latin cipher) THIS IS A CIPHER ---> T I I A I H R (Railfence cipher) H S S C P E X
It is this latter (16th century) two-dimensional transposition cipher that is widely used in modern cipher-systems, not the late medieval ‘anagrammatical’ transposition cipher.
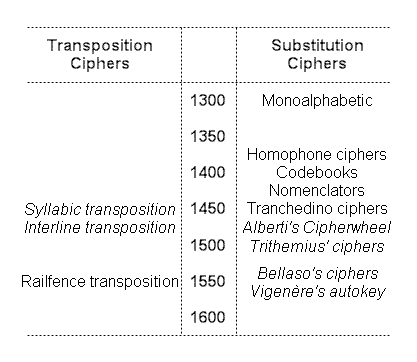
Older histories of cryptography tended to situate all these cipher techniques within what I call a “progressivist mythology” – the mistaken notion that every new idea not only flows out of all previous ideas, but also improves and refines them. In practice, of course, that’s not how things work : many brief local flowerings of ideas (basically, all the cipher varieties marked in italic above) made almost no impression on contemporary cryptographic practice. Even Vigenère’s autokey cipher (taught on every modern cipher course) did not get picked up by cryptography practitioners for more than two hundred years!
And now for the punchline of this post: if you discard the progressivist mythology, the range of possible local enciphering strategies for a given ciphertext is sharply constrained by the date and position of a document.
I argue that the Voynich Manuscript ciphertext is likely a prime example of this: its internal evidence dates it no earlier than 1450 and no later than 1470 – right at the time of the brief flowering of the kind of syllabic and interline transposition ciphers mentioned by Alberti in his De Componendis Cyfris (1467).
And so, if we seek to apply “pure” modern substitution cipher analytical techniques to something built around an unknown transposition cipher system, we would surely fail to make any sense of it – and this is, I believe, what has happened in the case of the VMs… why it has remained a “cipher mystery” for so long.