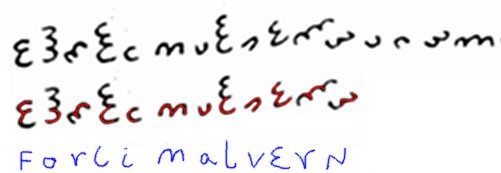Despite The Dorabella Cipher‘s brevity, its link to composer Sir Edward Elgar (who wrote it) has brought it a cult following over the years. Like other unbroken ciphers, it has appeared as a mysterious motif in TV plays, novels, and even recently in a children’s book (The Orphan of the Flames).

At first sight, it looks to be merely a straightforward simple substitution cipher of the kind that pen, paper, and an agile mind should crack relatively quickly. But what is mystifying is that even though Elgar apparently used precisely the same pigpen-like (3 sets of 8 orientations each) cipher alphabet elsewhere in his writings and notes, the letter-for-symbol replacements he used there make no sense when applied to his Dorabella Cipher. The key seems to match the lock, but doesn’t open the gate.
Moreover, given that the ciphertext’s statistical distribution sits awkwardly with those of natural languages, code-breakers’ numerous attempts to shoehorn their preferred substitutions into the cipher’s three short lines come across as clunky and false (at best). Worst of all, I’m sorry to say that even prolific cipher-solver Tony Gaffney’s ingenious and elegantly-structured decryption failed to please pretty much anyone apart from him.
However, the upside to all that grim cryptanalysis is the indisputable truth that Elgar messed around with language quite a lot, typically in a playful and mischievous way. In general, he loved subverting the rules of language, speech and music, which arguably culminated in his famous Enigma Variations, which some people like to call ‘musical cryptograms’ because many lightly parody (for example) various close friends’ speech and laughter rhythms.
Yet what has long tipped my own judgment against the Dorabella Cipher’s being a cipher of any sort is that by 14th July 1897 (the date of the note), Elgar (who wrote the note) hadn’t known Dora Penny (to whom or for whom the note was written) very long at all; and they never communicated in any kind of cipher before or after that date. But even so, my opinion was no more than a hunch, based only on various modern references on Elgar’s life I’d read… not very satisfactory, but that’s how these things tend to go.
Anyway, having spent far too long reading and relying on secondary sources on this particular cipher mystery, a few weeks ago I decided to instead go right to the source of the story – Dora Penny’s book “Edward Elgar: Memories of a Variation” (I bought a copy of the 1946 second edition, which has rather more information about the Enigma Variations than the first edition), written under her married name “Mrs Richard Powell”.
What I read there only served to strengthen my historical argument against The Dorabella Cipher’s being a cipher at all. Elgar and Penny first met on 6th December 1895, and the cipher was only the third letter Elgar ever wrote to Dora (if indeed, as she points out, it is a letter at all). (Also, he only started calling her “Dorabella” in 1898, so there’s a case to be made that its name isn’t chronologically accurate… oh well!) From all I could see, it would defy common sense if he had sent her something written in an deliberately intractable cipher: no matter how much of a fascination he personally had with such things, cryptography of any sort was not a discussion subject the two friends seemed to have shared at all.
And yet what we see does so resemble an enciphered cryptogram, a paradox which ultimately gives it its place at the Cipher Mysteries top table: for it really ought to be a simple cipher, but it surely is not one. And I find it hard not to hear Elgar’s voice saying to Dora Penny exactly what he said to her about the Enigma Variations (one of which is ‘hers’) – that surely she “of all people” would be able to unwrap its central mystery, its hidden themes. Wouldn’t his cipher, too, be steganography – hidden in plain sight?
As to the content of the note, I don’t believe that the newly married Elgar would have sent Dora Penny, for all the fun they had together (going out to the races, seeing Wolverhampton Wanderers, reading maps, flying kites, etc) a love letter. So in all probability, I think that what we are looking at here is a three line note or letter from him to her, in broadly the same joking and playful manner that he adopted in his other letters to her (though probably not as Byzantine in lexicographical complexity as later letters would become), regardless of the particular manner in which that effect is achieved.
The only other clue I have to offer is that in July 1897, the Elgars were living in a house called “Forli” (named after the talented Renaissance painter Melozzo da Forli, who incidentally gets mentioned a few times in Elizabeth Lev’s rather good The Tigress of Forli) in Malvern in Worcestershire. And so I wondered whether “Forli” and/or “Malvern” might be effective as cribs into the cryptogram, for Elgar would typically head even very short notes with his current address (several of which are charmingly reproduced as inserts in Dora Penny’s book). OK, it’s not quite “HEILH ITLER” at the start of Enigma messages, but you gotta work with what you’ve got, right? 🙂
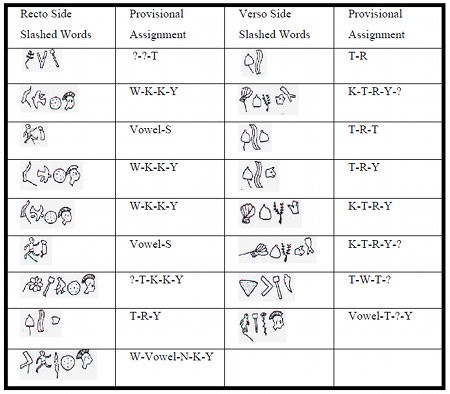
And so with all these fragmentary clues in mind, I stared and stared and stared at the Dorabella Cipher, trying to see what Elgar (mistakenly) thought Dora Penny would see straight away. And then I stared somemore. After a (fairly long) while, here’s what I noticed:-
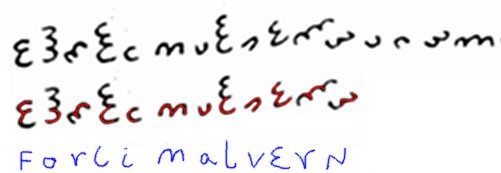
Essentially, I suspect that Elgar was so certain that Dora Penny would know what he would be saying in a short note that all he felt he needed to do was to write the general form of the words (even presented in the form of a ciphertext-like medium) and she would still be able to ‘read’ them. [Unfortunately, this proved not to be true!] So, I believe that what we are looking at could well be more like Elgar’s improvised steganographic attempt at a mind-reading trick than a traditional ciphertext per se. Such a process would (probably) produce something like what we see: a non-mathematical stegotext that fails to have the kind of rigorous statistical profile that “proper” ciphers would.
I’m the first to admit that it’s far more of a wobbly observation and a loose speculation than a rigorous proof: but what I’m proposing is that the Dorabella Cipher could turn out to be a quite different class of object from that which code-breakers have been trying (unsuccessfully) to crack. It’s not the end of the road here, but it might possibly be the very start of one… hopefully we shall see! 🙂