The story of how Ricky McCormick was found dead with two (apparently enciphered) notes in his pocket hit the news a while back, but I hesitated to write it up as a cipher mystery at the time because I didn’t think the media coverage was even remotely reliable. But revisiting the whole affair recently, I found a simply splendid online article courtesy of the River Front Times called “Code Dead” (by Christopher Tritto), which turned my opinion of the whole case right round.
This revealed…
* that McCormick had just travelled back from Florida, from where he had allegedly brought back baseball-sized zip-lock bags of marijuana for Baha Hamdallah, brother of the owner of the gas station where McCormick worked.
* that he was closely associated with some violent (if not actually sociopathic) individuals, such as Gregory Knox
* that the stretch of road his body was found on was used for dumping dead bodies both before and after his death
* that the FBI’s Cryptanalysis and Racketeering Records Unit (CRRU) sat on the two mystifying notes for 12 years before announcing their existence
* that McCormick’s family knew nothing about the notes until they heard them mentioned on the news. (“Now, twelve years later, they come back with this chicken-scratch shit.”)
Moreover…
* McCormick fathered two children with a girl he called “Pretty Baby” before she was 14 (for which he went to prison)
* he experienced chest pains and shortage of breath the week before he died, severe enough for him to check into ER. (Though admittedly he had smoked “at least a pack of cigarettes a day” since he was ten, and typically drank “more than twenty caffeinated beverages a day”).
* McCormick could hardly read or write when he left school. (“The only thing he could write was his name”, and that Ricky “couldn’t spell anything, just scribble.”)
Coincidentally, everyone’s favourite crypto-gal Elonka Dunin lives close to where McCormick’s body was left, and she’s taken an interest in the cipher mystery aspect of the case, even doing a video interview for the River Front Times explaining how monoalphabetic substitution ciphers work (not that that’s what we’re looking at here, *sigh*). But having learnt more about McCormick’s background and situation, she concludes “I don’t think McCormick wrote these notes”, and that “[P]erhaps he was a courier.”
(If you haven’t seen the notes before, the two thumbnails below link to decent quality scans of them – well worth opening up in a browser to see what all the fuss is about.)
So, what *are* we looking at here? Well, the Internet (as always) has plenty of commentary to wade through. The CRRU’s Dan Olson points out that “There are many E’s… that could be used as a spacer”: while Elonka notes the plethora of patterns periodically peppering the pages (such as “WLD”, “NCBE”, “SE” etc). There are also lots of bracket pairs (which have somehow led to the suggestion that it may in part be lists) as well as punctuation marks, most notably an apostrophe, which would loosely imply that the word preceding it (“WLD”) may well be a noun.
Olson seems convinced that the writer of the notes was ingenious and calculating, while Elonka too appears to think that they are of a complexity that would have been beyond McCormick’s abilities. Respectfully, I have to disagree: for I suspect that the main key to the notes’ impenetrability lies not in paranoia or secrecy but in a probable explanation for why McCormick failed school (and, conversely, why school failed McCormick) – dyslexia.
Look again at three highly structured consecutive lines from the notes:
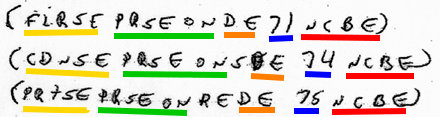
To me, this looks a lot like a mixed-up version of:-
* FIRSE PERSON D 71 NCB[E]
* SECND PERSON’S D 74 NCB[E]
* TRD’S PERSON R D 75 NCB[E]
Specifically, I think “NCB” will turn out to be a local address in St Louis (maybe even initials for Clinton Peabody?) – and if that’s right, why would the numbers not be the flat / house numbers of people buying drugs? McCormick preferred moving round at night (like “a vampire”), and he carried and held big bags of marijuana from Orlando for Baha Hamdallah (according to McCormick’s girlfriend), so the suggestion that he might have been some kind of small-time drug runner or dealer probably isn’t totally wild.
I don’t know, though: it’s all just awful. Victorian-era historians saw their job as weaving narratives around Events In History for the moral edification and correct instruction of Society In General, and even many moderns would find it journalistically tempting to take McCormick’s life of denial and ignominious death as launching pads for some glib commentary on a whole set of social macro-epidemics – guns, drugs, poverty, social inequality, education, dyslexia, whatevuh.
But all I’m actually left with is a feeling of deep sadness – that what we’re glimpsing into in these two notes is the life of a poor, illiterate guy who aspired to ride the horse of opportunity, but only ever got dragged behind it.
So, what strikes me most powerfully is that quite unlike other cipher mysteries, I don’t actually want to read what was written on McCormick’s two notes. I understand people often feel a deep-seated need for closure, but does any kind of (capital-j) Justice have the power to right the wrongs of these slow-motion train-wrecks?


