What has Barack Obama got to do with the Somerton Man (an unidentified man found dead on a beach south of Adelaide in 1st December 1948)?
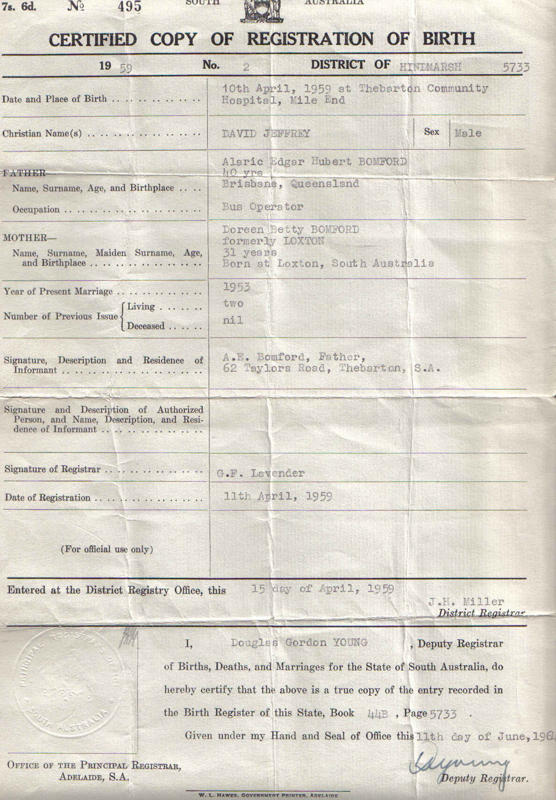
The surprising answer (as of a couple of days ago) is that people have tried adapting the same South Australian birth certificate (that of a certain David Jeffrey Bomford, born in Adelaide in 1959) to undermine or falsify both of their histories.
Obama Mama
The story about President Obama’s faked-up Kenyan birth certificate is well-known, though I don’t believe it has yet been definitely told anywhere. What happened is that a group of conspiracy theorists (known in the United States as “Birthers”) asserted before Obama’s election in 2008 that he had been born in Kenya (not Hawaii), and so was ineligible to be elected. All that was preventing their taking him to court was the lack of any supporting evidence…
So when, in mid-2009, digital photos of what appeared to be Obama’s Kenyan birth certificate appeared, Birthers (specifically Orly Taitz) were quick to rush them to court to submit appropriate motions for his disqualification etc. However, the suitably-embossed and plausibly-aged document shown in those images was (of course) a hoax.
KenyanBCPunkster
A while later, the creator of the fake document apparently surfaced as a commenter answering questions about the whole affair on the Free Republic website, under the pseudonym “KenyanBCPunkster”. So, without further ado, let’s try the obvious question first: why would he (I’m using “he” for convenience here, but I don’t actually know either way) do such a thing? His answer:-
It was after having been exposed to the whole “Birther” saga.
I watched as people would get the Birthers all worked up claiming they had finally found the smoking gun that would finally end the Obama candidacy, only for that smoking gun to never materialize. Like the Hawaiian birth certificate with Obama’s name as Barry Soetoro that some blogger claimed GOP operatives had got their hands on in Hawaii, the Michelle Obama tapes that Editor Korir claimed to have, etc.
One day I saw a “Birther” lamenting that they knew Obama was born in Kenya, but they just didn’t have the smoking gun.
I thought, what if they had one? If only for a little while. Then I thought what a smoking gun might look like. So I spent an afternoon one day and created it. Never having any idea that it would go as viral as it did. I figured it’d create a bit of a rumble in the blogosphere and then quickly die out.
(He also denied having been paid for making the fake document, or for posting on the Free Republic website.)
How he made it was also quite straightforward: “after a lengthy image search for [sensible-looking mid-20th century colonial] birth certificates” on Google Images, he found one that had been uploaded to a Bomford family tree website. Though it was from South Australia (specifically Adelaide) rather than Kenya, it was close enough to work with.
He then used the fields on that form as a starting point for creating his own Kenyan birth certificate-like document, filled the blanks out with an old typewriter (I think), added a plausible-looking embossed seal, aged it (probably with cold tea or something similar), and messed around with it for a bit until it basically looked the part. He added in another comment:-
I left some fields out that were in the original in order to make it better fit the aspect ratio of an 8-1/2 x 11 inch sheet of paper. I also used some of the same information for debunking purposes. Such as the “5733,” and the book and page numbers at the bottom. I kept the names of the registrar and district registrar, changing only their first initials. I made up the entire name of the deputy registrar to make it a Kenyan name.
So, what the guy did apparently was neither hugely sophisticated nor time-consuming: and by retaining details from the original certificate (such as the registrar’s surname etc), he pretty much ensured that it would be exposed before very long (as indeed it was). But, as he pointed out, it went far more viral than he thought. Sometimes these things just do – for example, it doesn’t take much of a geek angle for a page to get randomly Slashdotted, you just can’t tell in advance.
There was only one tiny bit of historical research he did, which was to pick a date (17th February 1964) “just after the time Stanley had filed for divorce from Obama Sr“. But Google helped him figure that out at speed, so that weren’t no big thang: his other comments betray a fairly nuanced understanding of US politics and politicians, so the rest he already knew.
Did the prank all go according to plan? Well… no, not really. When asked, he replied:-
[…] the one thing that has caused me to regret having done this […is that…] there are some out there who are so completely unhinged from reality that they actually believe that David Bomford’s birth certificate, that had been sitting on the Bomford family website for years before all of this, is the “fake.” […]
I only came here to set the record straight because I couldn’t believe there were people so gullible that even at this late date they’re still trying to claim it’s real even though I intentionally made it easy to debunk by most anyone who wasn’t completely detached from reality.
Incidentally, the nicest put-down from the 3500-post thread was when he was asked “Now why don’t you do something good with your talents?” His deadpan reply:-
I do.
Just so you know, the original David Bomford birth certificate image looked like this (though when the story went viral, it had to be taken down to prevent the server overloading), which I got from here:-
I Just Met A Troll Called “Maria”
So far so TL;DR. But compared to KenyanBCPunkster’s efforts, our recent Somerton Man hoaxer was a little more… Photoshop-centric, let’s say.
“Maria” (who posted the link to the image, and whose IP address has also been used to post comments to the blog under the name “Janice”, make of that coincidence what you will) did none of the tricky things that KenyanBCPunkster did to make his fake feel like a suitable historical artefact: in fact, what we’re looking at is a fairly crude bit of digital editing without much finesse.
However, what she (I assume “she”, but again I have no idea either way) did do reasonably well was to weave together the dates and places that people (and indeed trolls) would dearly like to be true about the secret history linking the Somerton Man and Jessie Harkness.
For instance, the age (41) and place of birth (Moscow) of the unnamed father were consistent with the Somerton Man and with Jessie’s recently-revealed ability to speak Russian: while the child’s year of birth (1942) was consistent with the year Jessie Harkness started at nursing school, etc. Its details dovetailed well enough with the facts to give it the immediate buzz of a real (but lost) thing, while the redacted grey rectangles helped it feel like something suppressed and slightly dangerous.
When I received it on Saturday morning, I approved it straightaway, and then took my son to his final ice skating lesson at Hampton Court Palace. (We got there early, and ended up having a lively discussion about which statues were old and which were modern, all very apposite.) I came home, looked at the alleged birth certificate full screen and saw immediately that it was a BFF (“Big Fat Fake”). *sigh*
But the whole experience led me to a horrible realisation. The thing about trolled hoaxes is that they encourage you to see what you want to see: and to my surprise, it turned out that what I actually wanted wasn’t a solution to the Tamam Shud cipher, but to be freed from waking up every morning to an blog inbox of sweary, unhappy, fake-id, delusional, nonsensical trolled comments, most of which come from individuals who plainly know better but choose to act worse. Shame on you.
In general, my own view of history has long been that only one question – “What happened?” (by which I mean what physically happened, as opposed to “what was going on in a particular individual’s head?”) – actually demands any attention, and any evidence that brings us closer to answering that question is a good thing.
Yet having said that, if trolls are prepared to fake evidence to support their wishful or delusional agendas and narratives, perhaps we should all give up and walk away. As I sometimes say, if you see a car about to crash, why jump inside it?