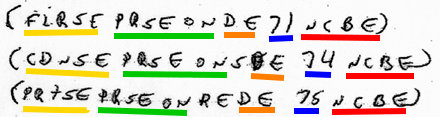Having recently written up the Moustier Cryptograms here (thanks to a declassified issue of the NSA’s in-house “Cryptolog” magazine), I bought a copy of Rudy Cambier’s (2002) book “Nostradamus and the Lost Templar Legacy“, simply because it appeared to contain just about the only thing written about Moustier in the last 40 years.
Initially, Cambier speculated that the cryptogram’s ten pairs of lines of scrambled text contained a somehow-obfuscated version of the Ten Commandments. But given that “the [two] Tablets abound with consonants” (p.132), he dropped that notion and instead hypothesized that the original author “might not have provided the vowels – through a well-known cryptographic expedient” (p.132), i.e. an abjad. Cambier then tells us that this hunch “actually appeared to be the case, and this is what may be considered quite a stroke of luck“, and that he decrypted them on that basis “on three winter evenings in December 1995, with a little effort and a little skill” (p.130).
But what does it say? He claims that the tables “indicate […] to the long-awaited one, to him who will be capable of deciphering them, the secret place where the [Knights Templar] belongings lie hidden” (p.130). Annoyingly, though, Cambier goes on to say that anyone interested in understanding how his lengthy argument goes should instead refer to the article by François Descy in “Le Courrier de l’Escaut” that ably summarizes it.
And therein lies a problem, in that there doesn’t seem to be a copy of this article online. On Le Courrier de l’Escaut’s website, it says that the paper has been following Cambier’s theories for many years, and that its first article covering them appeared on “le 11 février 1998”, but I don’t know whether or not that is the particular article to which Cambier is referring. I’ll try to get a copy, see what it says…
Anyway, according to local historian Jean Connart, work was undertaken on Moustier Church in June 1838 “in accordance with the plans of Philibert Pluvinage and Pierre Joseph Lemaitre”. But who were these two men, exactly?
I turns out that Philibert Pluvinage (b. 1770) was a lay clerk at Moustier Church and also Moustier Philharmonic Orchestra’s first conductor (in 1811). The Tournai archives hold an 1810 document describing Pluvinage’s church-related duties. It’s not clear if he married Françoise Joseph Lepoutte (b. 9th January 1766 Moustier, d. 30th October 1842), for I suspect “Philibert Joseph Pluvinage” was actually his father.
There’s a little more detail on Pierre Joseph Lemaître to be had:
* born & baptised 31st March 1741 in Moustier, Hainaut, Belgium.
* married Catherine Joseph Dehors on 5th May 1779. They had 11 children.
* got a law degree & became a lawyer at the Supreme Council of Hainaut.
* succeeded his father as clerk of Moustier (1794-1807).
* succeeded Willaumez as Mayor of Moustier (1807-1818).
* died 12th November 1822 in Moustier.
Hence it would seem that the 1838 work on the Church was carried out according to plans in part drawn up by the Mayor of Moustier at least 15 years earlier. But without actually seeing those plans (which may well be in an archive somewhere, you never know), that’s just about all we can say for the moment.
So… now that I’ve had a few days to think about this new (to me) cipher mystery, what do I think?
For a start, I have to say that I don’t believe that the two altars look even remotely medieval. Rather, apart from the apparently amateurish quality of their inscriptions, I think they resemble the kind of 18th/19th century monstrosities I recall seeing in churches all over France. (But please correct me if you think I’m wrong!). From the pictures in Cambier’s book, the two altars look to have been made from exactly the same material, by exactly the same builders, and at exactly the same time: so I don’t really buy into the notion suggested by Jean Connart that the St Martin’s altar may have been brought in from elsewhere (and then duplicated for the other altar). So, the only workable explanation I can currently see is that the two side altars were made together in 1838 following the collapse of the church roof during rebuilding work.
And yet the overall mystery remains… why on earth would a church of that general date have cryptograms on its altars?
Having pondered this for a while, I think the explanation will most likely turn out to be that these are imperfect copies of a much older pair of cryptograms that were in Moustier for many years. In fact, they may be not so much cryptograms as badly faded inscriptions (say, from the churchyard?), somehow tied up with the history of the church or town. As such, I suspect that we may stand little chance of deciphering them without an earlier (& hopefully less degraded) copy of them to work with. Hence I believe the best place to search for them would be in the pre-1838 notebooks or sketchbooks of Belgian antiquaries. Someone must have seen a pair of enigmatic inscriptions and copied them down, surely?
Yet I also have to note one odd possibility. Rudy Cambier’s book is all about how he believes Michel Nostradamus was simply an opportunist who took a much older book written in the Picard language (e.g. from the Franco-Belgian border area in the North) and adapted the verses to his contemporary French (Nostradamus was from Provence in the South). And, curiously, “Moustier” is directly mentioned in Nostradamus’ Century I, verse 95:-
Devant moustier trouvé enfant besson,
D´heroic sang de moine & vetustique:
Son bruit par secte langue & puissance son,
Qu´on dira fort eslevé vopisque.
Here, “besson” is an old-fashioned word for “jumeau” – twin. So this would seem to be talking about twin things in front of Moustier. OK, it’s a bit of a long shot, but… might this be a fragmentary fossil of a reference to the (admittedly putative!) earlier twin pair of inscriptions that ended up being (badly) duplicated in Moustier Church’s side altars? I don’t know, it could well be no more than a coincidence but… it’s an interesting thought, right? 😉