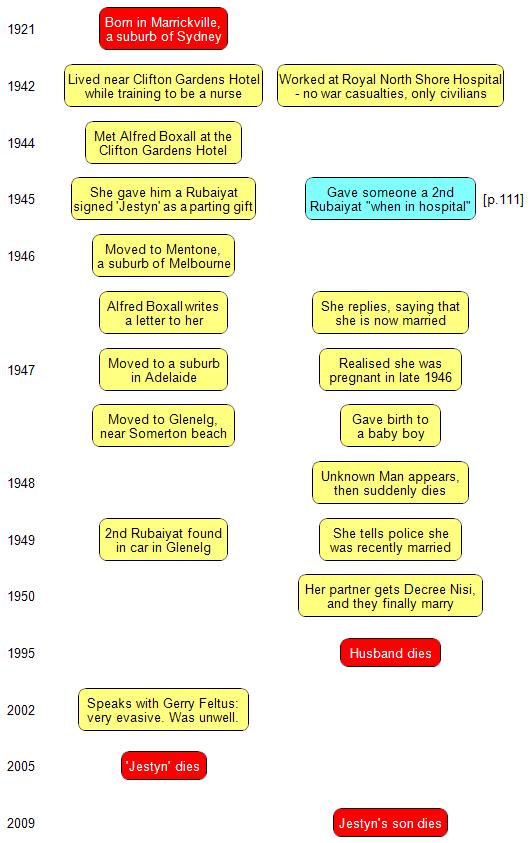
If you’ve followed parts one and two, you’ll know that I’m pretty sure that
(a) that The Unknown Man had worked on a ship (probably as a Third Officer), but was unemployed & nearly destitute;
(b) that Jestyn had probably first met him in the hospital where she worked, and – as with Alfred Boxall – had given him a copy of the Rubaiyat of Omar Khayyam, as well as her new phone number; and
(c) that he had recently been acutely ill, possibly even hospitalized following a bad virus.
Some other facts that strike me as relevant:
(d) the Somerton Man, Alfred Boxall, and Jestyn’s husband were all much the same age
(e) the Rubaiyat is a collection of love poetry
The first issue is why the Unknown Man travelled far across Australia to see a nurse who had once treated him, carrying a book of love poetry she had apparently given him, despite being unemployed and outrageously poor. Personally, I suspect the answer to this lies in the question: love. A number of people have speculated that the unknown Man had fathered the nurse’s son (some based on the observation that their earlobes apparently shared the same rare structure): travelling long-distance to see your own young son would be a perfectly consistent scenario.
But Jestyn now had a new partner, whom she consistently referred to as her “husband” (though it was to be several years before his divorce came through and they were able to marry). Given that she had already refused Alf Boxall’s request after the war to meet up with her, it seems odd that she allowed the Unknown Man to visit: why one and not the other? I believe this points to a different dynamic between her and the Unknown Man: indeed, if the Unknown Man were her young son’s father, I believe Jestyn wouldn’t comfortably have been able to turn him away, even if she did now have a partner she intended to marry.
All in all, I’m perfectly comfortable with the idea that this is what connected them together, and that rather than conspiracy or subterfuge, it was love that had bound him to her (even if it was not necessarily reciprocated): but what then are we to make of his mysterious enciphered note? After all, this is a cipher mystery, right?
MRGOABABD
MLIAOI
MTBIMPANETP
MLIABO AIAQC
ITTMTSAMSTGAB
For all the speculative and hallucinatory code-breaking efforts that have gone into cracking these few short lines, there’s no doubt in my mind what it actually is: nothing more than a performance aide-memoire, the first letters of a poem dedicated to Jestyn that the Unknown Man had himself written, perhaps composed on the train on his way over to Glenelg. In his mind, I suspect he was aspiring to something close to:-
“The Moving Finger writes: and, having writ,
Moves on: nor all thy Piety nor Wit
Shall lure it back to cancel half a Line,
Nor all thy Tears wash out a Word of it.”
Of course, few poets reach such sublimity and subtlety of expression, and I have little doubt that the Unknown Man’s own poetry fell well short of that league. But if it is a love poem, it seems a reasonably safe bet to me that each line has only four feet (there seem to be too few initials there for it to reach FitzGerald’s five feet per line), and so the lines probably also divide into four sets of two halves:-
MRGOA
— BABD
MTBIM
— PANETP
MLIABO
— AIAQC
ITTMTS
— AMSTGAB
Given that there’s a high chance that the letter [L] (which only appears once) probably stands for ‘[L]OVE’, I’d expect that [MLIABO] will turn out to be something not far off from “My Love Is Almost Boiling Over”. Intensely felt no doubt, but probably far from sublime.
Perhaps a retired crossword enthusiast with plenty of time on their hands might care to try to reconstruct this poem? There are plenty of reasonable clues to be had: [ITT] could well be not too far from “I Think That”; the last word of [BABD] probably rhymes with the last word of [PANETP], and similarly for [AIAQC] and [AMSTGAB]; the lines beginning [A-] could well be “AND…”, while [M-] could be “MY…”; the [Q] strongly constrains the [AIAQC] line; etc.
To sum up, I’m completely comfortable with the idea that the Unknown Man travelled to Glenelg not long after coming out of hospital to see Jestyn and their son, and that it was there he died, possibly poisoned by digitalis, but more likely from an allergic reaction to something in the pasty he’d had for lunch. But none of that really touches on the question of where he came from: really, what happened before the curtain rose on his relationship with Jestyn?
People don’t tend to speculate on this much, which is a shame because in many ways I think we do now have enough information to to give it a go. Perhaps the chewing gum he was carrying was the clue: for, as Diane O’Donovan thoughtfully pointed out in her comments to Part Two,
Well, I’d say that one thing is quite sure; he wasn’t Australian.
Gum-chewing was considered an exclusively American habit in the forties, and even into the sixties, positively loathed by most adults and by middle class teenagers too.
And if you tenaciously follow that idea through to the end…
So how about this? Mystery man is American, contracts malaria in the tropics and is sent to a hospital in Australia, as was usual. This first time, in Sydney. But then he gets orders to return to the front, prefers to go AWOL, gets caught and is put into an internment camp [perhaps already in Victoria; Melbourne Hospital was one of the internment camps. While there, he gets plenty of sun and exercise, but little really hard work. Fortunately, war ends. He’s finally tried for AWOL, but only sentenced to 12 months in prison (or gets sick again) so no sun for the final year.
Now released, he asks to be accepted as a new migrant, claiming to be a sign writer. He’s accepted, and buys the tools of the trade intending to start a new life and find Jestyn. Suitcase and clothes were given from a refugee/charity organisation, as part of a routine de-mob and welcome to Aus. etc.
BUT – While at Melbourne Hospital .. and so forth.
With my only proviso being that the Unknown Man was arguably more likely to be in the US Navy than the US Army, I think this is pretty much the best scenario currently going. Might the answer to the Somerton Man mystery therefore lie not in Australian hospital archives, but in US Navy files? As Diane muses, perhaps the most telling clue of all here might turn out to be the smallest: the pack of Juicy Fruit. Something to chew on! 😉